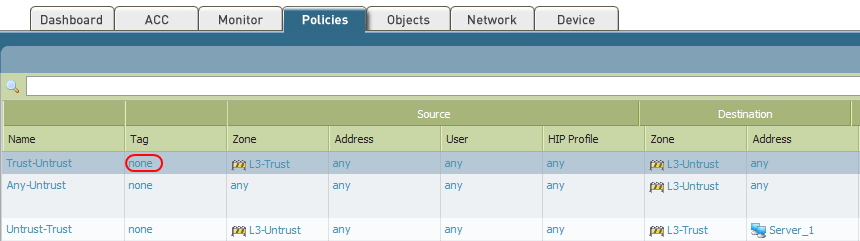
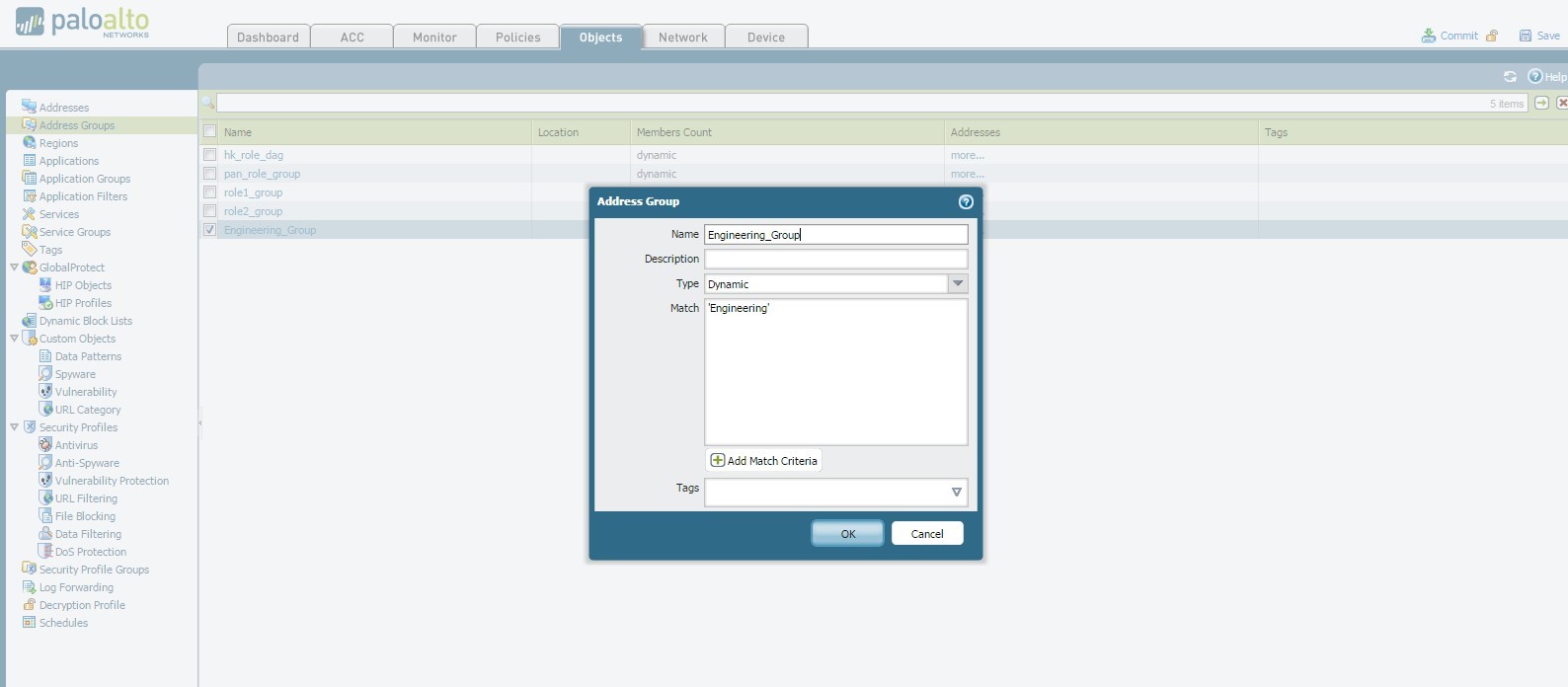
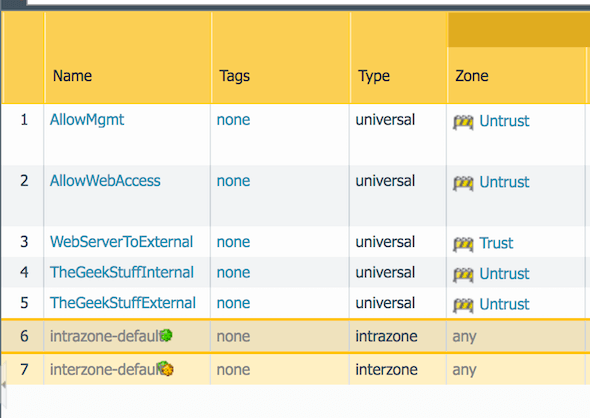
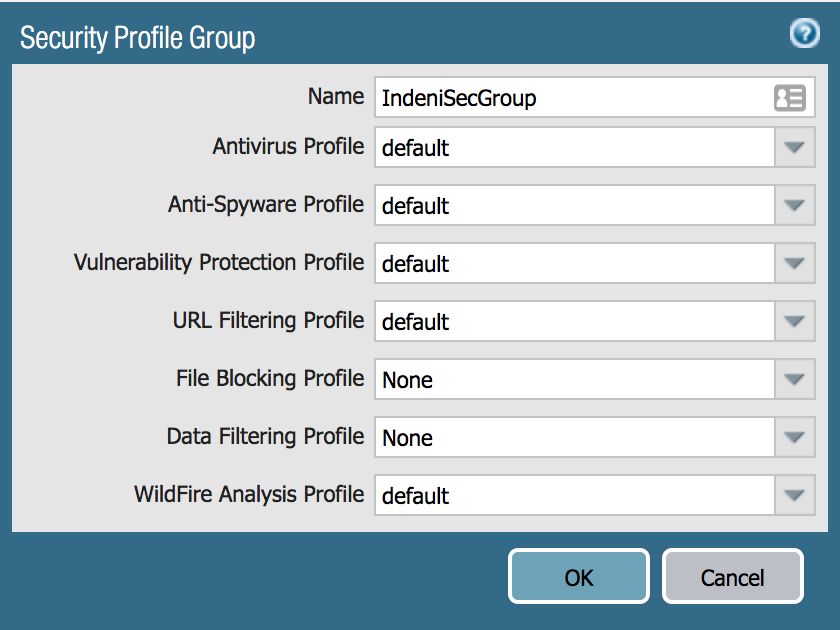
How to See Traffic from Default Security Policies in Traffic Lo... - Knowledge Base - Palo Alto Networks
How to See Traffic from Default Security Policies in Traffic Lo... - Knowledge Base - Palo Alto Networks

Multi-site with Cross-VC NSX and Palo Alto Networks Security - Network and Security Virtualization - VMware